-
General Knowledge
-
General Topics
- Abbreviations
- Books and Authors
- Famous Academies and Institutes
- First in India (Man)
- First in India (Women)
- Important Dates
- Famous Personalities
- Public Administration Science
- Astronomy
- Biology
- Botany
- Chemistry
- Physics
- Zoology
- Inventions and Scientists Geography
- Geographical Epithets India
- Geographical Epithets World
- Places Associated with Industries in India
- National Parks and Sanctuaries
- Towns on River Banks History
- Indian History and Culture
- Indian National Movement
- Indian Polity and Constitution
- Ancient Period in Indian History
- World History
- Governor General of India Culture
- Languages
- Indian Dance and Music
- Classical Dances of India
- Folk Dances in India and Tribal Dances in India
- Famous Dancers, Instrumentalists, Vocalists in India World
- First in the World
- Parliament Names
- United Nation Organizations (UNO)
- World's Famous News Agencies
- World Industries
- National Emblems
- Countries and Alternative Names
- Countries and Capitals
- View More topics...
- General Aptitude
- Problems on Ages
- Alligation and Mixture
- Area
- Arithmetic Progression
- Average
- Banker's Discount
- Boats and Streams
- Calendar
- Chain Rule
- Clock
- Compound Interest
- Decimal Fraction
- Height and Distance
- Logarithms
- Mensurations
- Numbers
- Odd Man Out and Series
- Partnership and Share
- Percentage
- Permutation and Combination
- Pipes and Cisterns
- Probability
- Problems on H.C.F and L.C.M
- Problems on Numbers
- Problems on Trains
- Profit and Loss
- Races and Games
- Ratio and Proportion
- Simple Interest
- Simplification
- Stocks and Shares
- Surds and Indices
- Time and Distance
- Time and Work
- True Discount
- Volume & Surface Areas
- General English
- Antonyms
- Synonyms
- Vocabulary Test
- One Word Substitution
- Sentence Completion
- Sentence Improvement
- Idioms & Phrases
- Homonyms
- Word Formation
- Active & Passive Voice
- Direct and Indirect Speech
- Spotting Errors
- Double Synonyms
- Choose the Appropriate Filter
- Spelling Test
- Transformation
- Reconstruction of Sentence
- Chooose the Correct or Incorrect Sentence
- Networking
- Interview Questions
-
Programming
- .NET
- Java
- ASP.NET
- C++
- Perl
- Python
- Ruby and Rails
- Struts
- Core Java
- Hibernate Database
- DB2
- MS SQL Server
- MySQL
- Oracle
- SQL
- DBMS
- Data Warehousing
- Data structures and Algorithms Cisco
- CCNA
- CCNP Routing
- CCNP Switching
- Internetworking
- Border Gateway Protocol Windows
- MCSE
- Exchange Server
- Windows Server 2008
- DNS & Active Directory
- Firewall Questions Linux
- Unix
- Linux Server Administrator
- Linux System Administrator
- Linux File Manipulation
- Database
- CCNA Routing Switching Online Test 1
- CCNA Routing Switching Online Test 2
- CCNA Routing Switching Online Test 3
- CCNA Routing Switching Online Test 4
- CCNA Routing Switching Online Test 5
- Home
- Online-Quiz
- Networking
- CCNA Routing and Switching
Instructions
- Total Questions 20
- Each question carry 1 mark
- Must answer all the questions (otherwise report card will not be generated)
- If you dont want to take a test, simply click the check answers button and view all the answers with explanations
- Do Not Refresh the Page
- No Time Limit
- Good Luck :)
Correct Answers :
[C]
Explanation :
The Point-to-Point Protocol (PPP) supports compression, authentication, error detection, and correction. PPP can detect errors in the transmission and request retransmission of the packets.
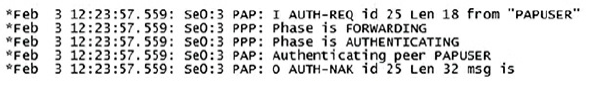
Correct Answers :
[C]
Explanation :
This is a debug of outgoing packets, and therefore the configuration problem is on this router. This router’s username must match the adjacent router’s hostname and both passwords must match.
Correct Answers :
[B]
Explanation :
The provider edge (PE) router is responsible for adding the MPLS label to a packet.
Correct Answers :
[B]
Explanation :
Virtual Private Networks (VPNs) are extremely scalable because they only require an Internet connection at each site. We can reuse the existing Internet connection at each site to create a site-to-site VPN tunnel.
Correct Answers :
[C]
Explanation :
The command service-policy USER-MAP out will configure the policy map called USER-MAP on the interface in an outbound direction
Correct Answers :
[D]
Explanation :
The web server’s IP address is referred to as the outside global address in reference to Network Address Translation (NAT).
Correct Answers :
[C]
Explanation :
The Network Time Protocol (NTP) defines 16 levels of stratums. A stratum of zero has absolute precision, such as an atomic clock, which also has little or no delay. When an NTP clock is timed off a stratum zero clock, it becomes a stratum one, and when an NTP clock is timed off of a stratum one, it becomes a stratum two. The process continues onward, adding a one to each slave unit, as delay increases and you move further away from absolute precision.
Correct Answers :
[C]
Explanation :
When Hot Standby Router Protocol (HSRP) is used, the default gateway the client is issued is an IP address for the virtual router. The virtual router is not a physical router, but it is mapped to a physical router via HSRP. The active router processes requests for the virtual router IP address by responding to the virtual MAC address associated with the virtual router IP address.
Correct Answers :
[C]
Explanation :
When interface tracking is turned on and a link that is being tracked fails, the priority of the active router is lowered, and an election is forced. This will make the standby router become the active router. However, if the link is repaired, the priority will recover to its normal value, but the current active router will remain the active router. Preemption allows for the value to instantly reelect the original router as the active router.
Correct Answers :
[B]
Explanation :
The Start of Authority (SOA) record establishes several key pieces of information, such as the primary DNS server, the timers for refreshing DNS entries, and a default time to live (TTL). The default TTL is used when a resource record is not explicitly configured with a TTL.
Correct Answers :
[D]
Explanation :
An attacker will take advantage of the automatic trunking configuration of Dynamic Trunking Protocol (DTP). This will allow the attacker to create a trunk with the switch and tag packets so that they can hop onto different VLANs.
Correct Answers :
[A]
Explanation :
When you are configuring port security on an interface, the switchport should have a mode of access configured. This will also protect the switch from transitioning into a trunk if another switch is connected.
Correct Answers :
[C]
Explanation :
Port security can prevent MAC address flooding attacks by restricting the number of MAC addresses associated to an interface. This will prevent the Content Addressable Memory (CAM) from being overrun by bogus entries.
Correct Answers :
[A]
Explanation :
The command access-list 101 deny tcp 192.168.2.0 0.0.0.255 any eq 23 will deny TCP traffic from 192.168.2.0/24 to any address with a destination of 23 (Telnet). The command access-list 101 permit ip any any will permit all other traffic.
Correct Answers :
[B]
Explanation :
Conventional access lists lack the ability to edit a single entry. The entire ACL must be removed and re-added with the correct entry. An alternative to conventional access lists is named access lists. A named access list is referenced by line numbers, which allows for removal and additions of single entries.
Correct Answers :
[A]
Explanation :
Trap messages are sent from Simple Network Management Protocol (SNMP) agents to the network management station (NMS). This happens when an event that the router or switch is set to alert the NMS about is triggered. An example of this is overheating of the switch or an important link going down.
Correct Answers :
[B]
Explanation :
Simple Network Management Protocol version 2c lacks security. The only mechanism you can employ for security is complex community names. Security was introduced in version 3 of SNMP.
Correct Answers :
[B]
Explanation :
The command interface range gigabitethernet 1/1 - 12 will allow you to configure the interfaces Gigabit Ethernet 1/1 to 1/12.
Correct Answers :
[D]
Explanation :
The default syslog facility level is debug 7. All debug messages are logged to the internal buffer by default.
Correct Answers :
[C]
Explanation :
The command ip ftp username USER will configure the username USER for FTP connections. The command ip ftp password USERPASS will configure the password USERPASS for FTP connections.
|
|
||||||||||||||||||||||||||||