-
General Knowledge
-
General Topics
- Abbreviations
- Books and Authors
- Famous Academies and Institutes
- First in India (Man)
- First in India (Women)
- Important Dates
- Famous Personalities
- Public Administration Science
- Astronomy
- Biology
- Botany
- Chemistry
- Physics
- Zoology
- Inventions and Scientists Geography
- Geographical Epithets India
- Geographical Epithets World
- Places Associated with Industries in India
- National Parks and Sanctuaries
- Towns on River Banks History
- Indian History and Culture
- Indian National Movement
- Indian Polity and Constitution
- Ancient Period in Indian History
- World History
- Governor General of India Culture
- Languages
- Indian Dance and Music
- Classical Dances of India
- Folk Dances in India and Tribal Dances in India
- Famous Dancers, Instrumentalists, Vocalists in India World
- First in the World
- Parliament Names
- United Nation Organizations (UNO)
- World's Famous News Agencies
- World Industries
- National Emblems
- Countries and Alternative Names
- Countries and Capitals
- View More topics...
- General Aptitude
- Problems on Ages
- Alligation and Mixture
- Area
- Arithmetic Progression
- Average
- Banker's Discount
- Boats and Streams
- Calendar
- Chain Rule
- Clock
- Compound Interest
- Decimal Fraction
- Height and Distance
- Logarithms
- Mensurations
- Numbers
- Odd Man Out and Series
- Partnership and Share
- Percentage
- Permutation and Combination
- Pipes and Cisterns
- Probability
- Problems on H.C.F and L.C.M
- Problems on Numbers
- Problems on Trains
- Profit and Loss
- Races and Games
- Ratio and Proportion
- Simple Interest
- Simplification
- Stocks and Shares
- Surds and Indices
- Time and Distance
- Time and Work
- True Discount
- Volume & Surface Areas
- General English
- Antonyms
- Synonyms
- Vocabulary Test
- One Word Substitution
- Sentence Completion
- Sentence Improvement
- Idioms & Phrases
- Homonyms
- Word Formation
- Active & Passive Voice
- Direct and Indirect Speech
- Spotting Errors
- Double Synonyms
- Choose the Appropriate Filter
- Spelling Test
- Transformation
- Reconstruction of Sentence
- Chooose the Correct or Incorrect Sentence
- Networking
- Interview Questions
-
Programming
- .NET
- Java
- ASP.NET
- C++
- Perl
- Python
- Ruby and Rails
- Struts
- Core Java
- Hibernate Database
- DB2
- MS SQL Server
- MySQL
- Oracle
- SQL
- DBMS
- Data Warehousing
- Data structures and Algorithms Cisco
- CCNA
- CCNP Routing
- CCNP Switching
- Internetworking
- Border Gateway Protocol Windows
- MCSE
- Exchange Server
- Windows Server 2008
- DNS & Active Directory
- Firewall Questions Linux
- Unix
- Linux Server Administrator
- Linux System Administrator
- Linux File Manipulation
- Database
- CCNA Routing Switching Online Test 1
- CCNA Routing Switching Online Test 2
- CCNA Routing Switching Online Test 3
- CCNA Routing Switching Online Test 4
- CCNA Routing Switching Online Test 5
- Home
- Online-Quiz
- Networking
- CCNA Routing and Switching
Instructions
- Total Questions 20
- Each question carry 1 mark
- Must answer all the questions (otherwise report card will not be generated)
- If you dont want to take a test, simply click the check answers button and view all the answers with explanations
- Do Not Refresh the Page
- No Time Limit
- Good Luck :)
You Scored % - /
Correct Answers :
[B]
Explanation :
Structured Query Language (SQL) operates at the Session layer of the OSI model. It uses half-duplex communications to request data and receive the reply. Other examples of Session layer protocols are Network File System (NFS), Server Message Block (SMB), and NetBIOS.
Correct Answers :
[D]
Explanation :
The 802.11ac protocol will be least likely to overlap the wireless channels the tenants are using. The 802.11ac protocol uses the 5 GHz wireless frequency spectrum. The 5 GHz spectrum defines 24 non-overlapping wireless channels. The 2.4 GHz spectrum defines 11 channels, but only 3 of them are non-overlapping. Although 802.11n operates on 2.4 GHz and 5 GHz, 802.11ac only operates on 5 GHz. Therefore, 802.11ac will have the least likely overlap of current channels.
Correct Answers :
[C]
Explanation :
Flow control is a function of the Transport layer of the Open Systems Interconnection (OSI) model. User Datagram Protocol (UDP) operates at the Transport layer. UDP provides a program with a connectionless method of transmitting segments. TCP is a connection-based protocol and maintains a state throughout the transfer of data.
Correct Answers :
[C]
Explanation :
Platform as a Service (PaaS) is commonly used by software developers. It provides a development platform that the software developer can use to create applications. An example of this is a web server with PHP and MySQL, which is hosted in the cloud.
Correct Answers :
[D]
Explanation :
Crossover cables are wired with the 568B specification on one side, and on the other side, the 568A specification is used. This change in wiring delivers the TX pair on pins 4 and 5 to the RX pair on pins 1 and 2. Straight-through cables are wired with the 568B specification on one side, and on the other side, the 568B specification is used.
Correct Answers :
[A]
Explanation :
Stateless Address Autoconfiguration (SLAAC) relies on the Neighbor Discovery Protocol (NDP). NDP works by using multicast and ICMPv6 message types. The host will multicast to ff02::1 an ICMPv6 Router Solicitation (RS) message, and the router will respond with a Router Advertisement (RA) message. This response will allow the host to obtain the network address and gateway of the network. The host will then create a host address portion of the IPv6 address and use the Duplicate Address Discovery (DAD) protocol to check for a duplicate address.
Correct Answers :
[B]
Explanation :
The IPv6 address 2202:0ff8:0002:2344:3533:8eff:fe22:ae4c is an EUI-64 generated address. The host portion of the address is 3533:8eff:fe22:ae4c, the fffe in the middle of it depicts that the address was generated from the MAC address. The MAC address of this host would be 37-33-8e-02-ae-4c. When EUI-64 is used, an ffee is placed in the middle of the MAC address, and then the 7th bit from the left is flipped. This changes the first two hex digits of the MAC address from 35 to 37.
Correct Answers :
[C]
Explanation :
The network 192.168.4.32/27 has a valid IP address range of 192.168.4.33 to 192.168.4.62. The /27 CIDR notation, or 255.255.255.224 dotted-decimal notation (DDN) defines networks in multiples of 32. Therefore, the address 192.168.4.28/27 is part of the 192.168.4.32/27 network.

Correct Answers :
[B]
Explanation :
The first field after the preamble and Start Frame Delimiter (SFD) is the destination MAC address. The destination MAC address is always first because switches need to make forwarding decisions upon reading the destination MAC address.
Correct Answers :
[A]
Explanation :
The forward/filter function of a switch is used to look up the destination MAC address in a MAC address table and decide the egress interface for the frame. If the MAC address is not in the table, the frame is forwarded out all of the interfaces. When the client responds, its source MAC address will be recorded in the MAC address table for future lookup.
Correct Answers :
[B]
Explanation :
Access ports strip all VLAN information before the frame egresses the destination interface. The endpoint on an access switchport will never see any of the VLAN information that was associated with the frame.
Correct Answers :
[D]
Explanation :
The command switchport trunk allowed vlan 12 will remove all other VLANs and only VLAN 12 will be allowed on the trunk interface. The proper command to add an additional VLAN would be switchport trunk allowed vlan add 12. This command will add a VLAN to the already established list.
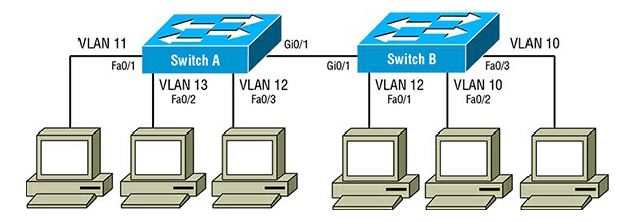
Correct Answers :
[B]
Explanation :
Switch A and Switch B are participating in VLAN tagging. Therefore, Switch A interface Gi0/1 and Switch B interface Gi0/1 are both configured as trunk switchports. This will allow VLAN tagging across the trunk link.

Correct Answers :
[C]
Explanation :
Switch B has the lowest MAC address of all of the switches. Therefore, Switch B will become the RSTP root bridge. All ports leading back to Switch B will become the root ports. Switch A interface Gi1/8, Switch D interface Fa2/16, and Switch C interface Gi1/3 will become root ports.
Correct Answers :
[B]
Explanation :
When you configure the switchport to a mode of access, you are statically configuring the interface to remain an access switchport. When you configure the switchport to nonegotiate, you are turning off Dynamic Trunking Protocol (DTP). The switch will never negotiate its switchport.
Correct Answers :
[A]
Explanation :
The command channel-group 1 mode passive configures the port to be placed in a passive negotiating state. The other switch must be placed into an active negotiating state for LACP to become the control protocol for the channel group.
Correct Answers :
[B]
Explanation :
When BPDU Guard is configured on a port, it guards the port from creating a loop. It also guards STP so that the STP calculation of redundant links is not affected by the device connect to the interface. If a BPDU is seen on the interface, the interface will immediately enter into an err-disable state. The most likely cause was that another switch was plugged into the interface.
Correct Answers :
[D]
Explanation :
The VLAN Trunking Protocol assists in synchronizing a VLAN database across all Cisco switches participating in VTP. You must initially configure the VTP domain on the switch that will hold the master database. Then all other switches must be configured as clients and the VTP domain must be configured as well.
Correct Answers :
[C]
Explanation :
The 802.1w Rapid Spanning Tree Protocol defines that designated switchports always forward traffic. The designated port is a port that is forwarding traffic and is opposite of the root port or blocking port if it is a redundant link.

Correct Answers :
[B]
Explanation :
There is a total of three frames that are encapsulated during the process of Host A sending a packet to Host B. In the exhibit, there are two hubs and two routers. The first frame is encapsulated from A to Router A. The second frame is encapsulated from Router A to Router B. The third frame is encapsulated from Router B to Host B.
|
|
||||||||||||||||||||||||||||