- Home
- Networking
- CWSP-205
26.
Laura is attempting to diagnose a WLAN by using a packet analyzer to capture the exchange
of frames and packets between a wireless client and the AP. In the process of analyzing the
packets, she sees two 802.11 authentication frames, two 802.11 association frames, and
DHCP requests and responses, and then she begins to see encrypted data. Which of the following
could the client be using? (Choose all that apply.)
- A.Open System authentication
- B.Shared Key authentication
- C.802.1X/EAP
- D.WEP
- E.IPsec
- Answer & Explanation
- Report
Answer : [A, E]
Explanation :
Explanation :
| Since there are only two 802.11 authentication frames, Open System authentication is being used. Shared Key authentication would generate four 802.11 authentication frames. If 802.1X/EAP or WEP were being used, then the client would be doing Layer 2 encryption and the DHCP frames would be encrypted and not visible. Therefore, 802.1X/EAP and WEP are not being used. IPsec VPNs utilize Layer 3 encryption that would allow Laura to see the DHCP exchange and any other IP traffic. |
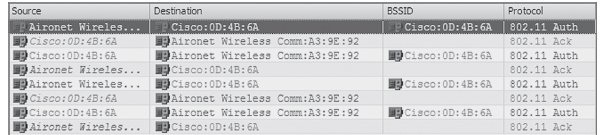
27.
This graphic shows a packet capture of a successful 802.11 authentication. In which of the following
types of client connections could this authentication not occur? (Choose all that apply.)
- A.802.1X/EAP
- B.WEP with Shared Key authentication
- C.WEP with Open System authentication
- D.Open System authentication with WEP
- Answer & Explanation
- Report
Answer : [A, C, D]
Explanation :
Explanation :
| The graphic shows an 802.11 Shared Key authentication that is made up of four authentication frames: an authentication request followed by a cleartext challenge frame, followed by a challenge response with the cleartext data encrypted, followed by an authentication response. 802.1X/EAP works together with Open System authentication but cannot be deployed when WEP is used. In order to use Shared Key authentication, WEP must be enabled. Shared Key authentication is optional with WEP, although not recommended. |
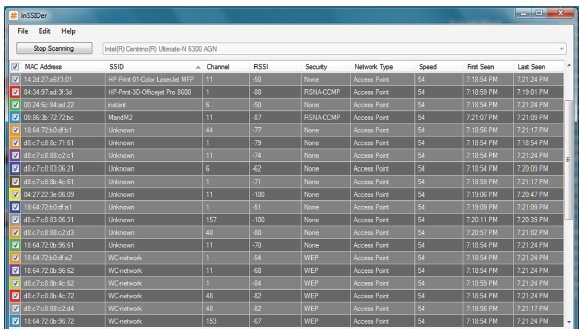
28.
This graphic shows a WLAN discovery tool screen capture. How many SSIDs are configured
with cloaking enabled? (Choose all that apply.)
- A.None
- B.At least ten
- C.One
- D.Ten
- E.Exact number cannot be determined
- Answer & Explanation
- Report
Answer : [B, E]
Explanation :
Explanation :
| The WLAN discovery utility displays the SSID field with a value of Unknown ten times. These are hidden or cloaked networks. Cloaking the SSID usually keeps the SSID hidden from most WLAN discovery tools that use null probe requests. Any of the SSIDs shown could be hidden; however, since hiding an SSID does not guarantee that it cannot be seen, from this screen there is no way of knowing which, if any, of the other SSIDs are configured for cloaking. Because hidden SSIDs are still transmitted in cleartext in some 802.11 management frames, a protocol analyzer can always find a hidden SSID. Even simple WLAN discovery tools may sometimes discover hidden SSIDs. |
29.
128-bit WEP encryption uses an IV and a static key. What are the lengths of these?
- A.64 bit IV and 64 bit key
- B.24 bit IV and 104 bit key
- C.28 bit IV and 100 bit key
- D.20 bit IV and 108 bit key
- E.None of the above
- Answer & Explanation
- Report
Answer : [B]
Explanation :
Explanation :
| 128-bit WEP encryption uses a secret 104-bit static key that is combined with a 24-bit Initialization Vector for an effective key strength of 128 bits. |
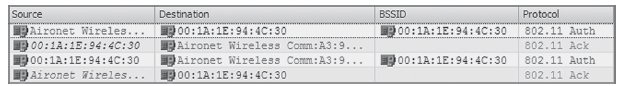
30.
The graphic shows a packet capture of a successful 802.11 authentication. In which of the
following types of client connections could this not occur?
- A.802.1X/EAP
- B.WEP with Shared Key authentication
- C.WEP with Open System authentication
- D.Unencrypted with Open System authentication
- Answer & Explanation
- Report
Answer : [B]
Explanation :
Explanation :
| The graphic shows a two-frame Open System authentication. 802.1X/EAP works together with Open System authentication. An unencrypted session uses Open System authentication. |